Azure Bastion is Microsoft's PaaS service that eliminates the need to expose your Azure virtual machines via public IPs for Remote Desktop (RDP) and Secure Shell (SSH) connections. Instead of leaving port 3389 or 22 open on the Internet - a favorite target of scan bots and bruteforce attacks - Bastion acts as a managed jump host that establishes TLS-encrypted sessions from the Azure portal or your native client.
The marketing pitch: "Enhanced security without complexity, one-click connection". The reality: a service that costs €140/month in SKU Basic to protect VMs you use for 2 hours a week, with frustrating limitations and cheaper but riskier alternatives. Between the classic self-hosted bastion (complex, time-consuming), direct public IP (dangerous), and Azure Bastion (simple but expensive), the choice is never obvious.
This article dissects Azure Bastion beyond the marketing hype: technical operation, actual pricing with hidden pitfalls, objective comparison with alternatives (public IP, jump box, VPN), use cases where Bastion is essential vs. situations where it is a waste of money. Because securing access to your VMs should not require a master's degree in network architecture or drain your cloud budget.
What is Azure Bastion and how does it work technically?
The classic RDP/SSH security problem
Traditional scenario: you create a Windows/Linux VM on Azure for a dev, test or production environment. To connect to it via RDP (Windows) or SSH (Linux), you have two options:
Option A - Exposed public IP: attach a public IP address to the VM and authorize port 3389 (RDP) or 22 (SSH) in the Network Security Group (NSG). Result: your VM can be scanned from anywhere on the Internet. Automated bots detect the IP within hours and launch dictionary attacks. Even with complex passwords or source IP restrictions, the attack surface is maximized.
Option B - Manual jump box: deploy a dedicated VM (the bastion/jump host) in a specific subnet, configure NSGs, manage security updates, maintain high availability. Improved security but heavy operational burden: OS patching, sizing, monitoring, 24/7 VM costs.
Azure Bastion architecture
Azure Bastion eliminates these compromises with a fully-managed PaaS architecture:
Deployment in AzureBastionSubnet Bastion is provisioned in a dedicated subnet named AzureBastionSubnet (minimum /26 or 64 IPs) within your VNet. This subnet contains Bastion instances (optimized VMs managed by Microsoft).
Connection via TLS proxy: when you initiate an RDP/SSH connection from the Azure portal, traffic passes via HTTPS (port 443) to the Bastion service. Bastion then establishes an RDP/SSH session to the target VM via its private IP. Your VM never needs a public IP. The flow is end-to-end encrypted using TLS 1.2+.
Agent- and client-free: no need to install an agent on target VMs or specific software on your workstation. RDP/SSH runs directly in the browser (HTML5) for portal connections, or via your native local RDP/SSH client (with the minimum Standard SKU).
Permissions and RBAC: Bastion respects Azure RBAC permissions. A user can only connect to the VMs to which he or she is entitled. No risk of a developer accessing production VMs by mistake.
Optional zonal architecture: deployment in several Availability Zones for high availability (preview in October 2025). If a zone goes down, connections switch over automatically.
The 4 SKUs: Developer, Basic, Standard, Premium
Bastion Developer (GA since June 2025): free lightweight SKU. Connection to 1 VM at a time via the Azure portal only. No AzureBastionSubnet required, no Bastion resource to deploy. Direct activation from the VM's "Connect" page. Perfect for test developers who want to avoid public IPs. Limitations: no connection via native client, no scaling, only one active session per user.
Bastion Basic (old standard version): deployment in AzureBastionSubnet, 2 instances by default (40 concurrent SSH or 20 RDP connections). Portal connection only, no native client. Price: ~€140/month (€0.19/hour) + outgoing data transfer.
Bastion Standard: all Basic features + connection via native RDP/SSH client (from your Windows Remote Desktop terminal/client), manual scaling up to 50 instances, file upload/download, IP-based connection support (connection to VMs outside VNet via peering), Shareable Link integration. Price: ~€140/month base + ~€70/additional instance.
Bastion Premium (new 2025): all Standard features + Session Recording (video recording of RDP/SSH sessions for auditing and compliance), Private-only Bastion (no public IP on Bastion itself, 100% private via Private Endpoint). Price: ~€200/month base + additional instances.
Real pricing and hidden traps: beyond €140/month
2025 pricing structure
Hourly cost SKU:
- Developer: free (GA since June 2025)
- Basic: €0.19/hour = ~€140/month
- Standard: 0.19€/hour = ~140€/month (2 instances included)
- Premium: €0.27/hour = ~€200/month (2 instances included)
Additional instances (Standard/Premium): €0.095/hour per instance = ~€70/month per scale unit. Each instance supports 20 RDP connections or 40 concurrent SSH connections (average load).
Outgoing data transfer: billed like all outgoing Azure traffic. First 100 GB: ~€0.08/GB. Over 10 TB: ~€0.05/GB. If you transfer large files via RDP (copy and paste 50 GB of data), expect to pay an additional €2-4.
Public IP: Basic/Standard/Premium require a Standard SKU public IP. Cost: ~€3.50/month. Developer does not require it.
Realistic total monthly cost calculation
Scenario 1 - Dev/test environment:
- 5 developers, 1 VM each, connection 2h/day
- Solution: Bastion Developer (free)
- Monthly cost: €0
Scenario 2 - SME production:
- 20 VMs, 5 system administrators, 10 simultaneous connections max.
- Solution: Bastion Standard (2 basic instances are all you need)
- Monthly cost: €140 + €3.50 IP + ~€10 data transfer = €153.50/month
Scenario 3 - Large company:
- 200 multi-region VMs, 50 admins, 30 simultaneous connections pic
- Solution: Bastion Premium with 4 instances (2 base + 2 additional)
- Monthly cost: €200 + (2 x €70) + €3.50 + €50 transfer = €393.50/month
Scenario 4 - Company with mandatory recording session:
- Financial or health compliance requiring audit of all admin sessions
- Solution: Bastion Premium with Session Recording enabled
- Video storage: Azure Storage at ~0.02€/Gb. 100h sessions/month = ~50 GB = 1€.
- Monthly cost: €200 + €3.50 + €1 storage + €15 transfer = €219.50/month
Hidden costs rarely mentioned
Dedicated subnet /26: immobilizes 64 IP addresses in your VNet address space. In heavily-used VNets, this may force an architectural redesign.
No SKU downgrade: once deployed in Standard or Premium, it's impossible to go back down to Basic without deleting and redeploying everything. If you test Premium "just to see", you're stuck with the Premium price.
Continuous billing: Bastion is billed by the hour as soon as it is deployed, whether you use it or not. VM off = Bastion bill running. Forget Bastion in a test environment → 140€/month waste.
Concurrent connection limits: Basic with 2 instances = 20 RDP or 40 SSH max. If you exceed, users wait in a queue. No automatic scaling like VMs, only manual. An unanticipated peak = users blocked.
Network bandwidth: high-resolution RDP connections (multi-screen, 4K) consume 5-10 Mbps per session. 10 simultaneous sessions = 50-100 Mbps. Check that your VNet and peering support the load.
Bastion vs Alternatives: a no-holds-barred comparison
Alternative 1: Direct public IP on the VM
Cost: ~€3.50/month per VM (Standard public IP) + a few cents for data transfer = €4/month
Advantages:
- 35x cheaper than Bastion Basic
- Ultra-low latency (direct connection)
- Compatible with all RDP/SSH tools without restriction
Disadvantages:
- Risque sécurité majeur : exposition Internet directe, cible des attaques automatisées en <24h
- Requires strict NSG with whitelisted source IP (problematic for nomad users)
- Logs of permanent intrusion attempts (background noise)
- Non-compliant with numerous security frameworks (ISO 27001, NIST, PCI-DSS)
Verdict: acceptable for a personal lab or disposable dev environment. Unacceptable for production or sensitive data. If your IT department discovers prod VMs with public IP + open RDP, prepare for an unpleasant conversation.
Alternative 2: Self-hosted Jump box (traditional Bastion)
Cost: VM B2s (2 vCPU, 4 GB RAM) = ~€35/month + public IP €3.50 = €38.50/month
Advantages:
- Total control: custom OS, custom logs, specific tools
- Predictable fixed cost
- No artificial limitations (competing connections, features)
Disadvantages:
- Operational workload: monthly patching, monitoring, hardening, user management
- SPOF (Single Point of Failure): if the VM goes down, no more access to other VMs
- Complex setup: NSG, UDR, deployment scripts, high availability requires 2+ VMs
- Security responsibility: logs, audits, compliance = your problem
Verdict: viable for mature IT teams with infrastructure skills. Counter-productive for dev teams or SMEs without dedicated OPS. The time spent maintaining a jump box costs more than Bastion's €140/month.
Alternative 3: VPN Point-to-Site or Site-to-Site
Cost: VPN Gateway Basic = ~€33/month. VPN Gateway Standard (best performance) = ~135€/month
Advantages:
- Full network access to VNet (not just RDP/SSH)
- Excellent latency once the tunnel is established
- Compatible with all protocols (not limited to RDP/SSH)
Disadvantages:
- Complex initial configuration (certificates, VPN client profiles)
- Requires VPN client installed on each user workstation
- Split-tunneling can expose corporate network if misconfigured
- Cost similar to or higher than Bastion for high-performance VPN Gateway
Verdict: Relevant if you already have a VPN for other uses (access to private services, databases). Overkill if your only need is occasional RDP/SSH.
Alternative 4: Azure Just-In-Time (JIT) VM Access
Cost: included in Microsoft Defender for Cloud (formerly Azure Security Center). Plan 2: ~€13/VM/month
Principle: temporarily opens RDP/SSH ports in NSG only when requested by an authorized user, for a limited time (1-3h). Source IP locked.
Advantages:
- Minimum exposure (ports closed 99% of the time)
- Coût inférieur à Bastion pour <10 VMs
- Access logs integrated into Defender
Disadvantages:
- VM retains a public IP (reduced attack surface, but still available)
- Defender for Cloud must be activated
- Latency: 30-60 seconds to obtain access after request
Verdict: excellent complement or alternative for small/medium environments. Can be combined with Bastion (JIT + connection via Bastion = double security).
Summary comparison table
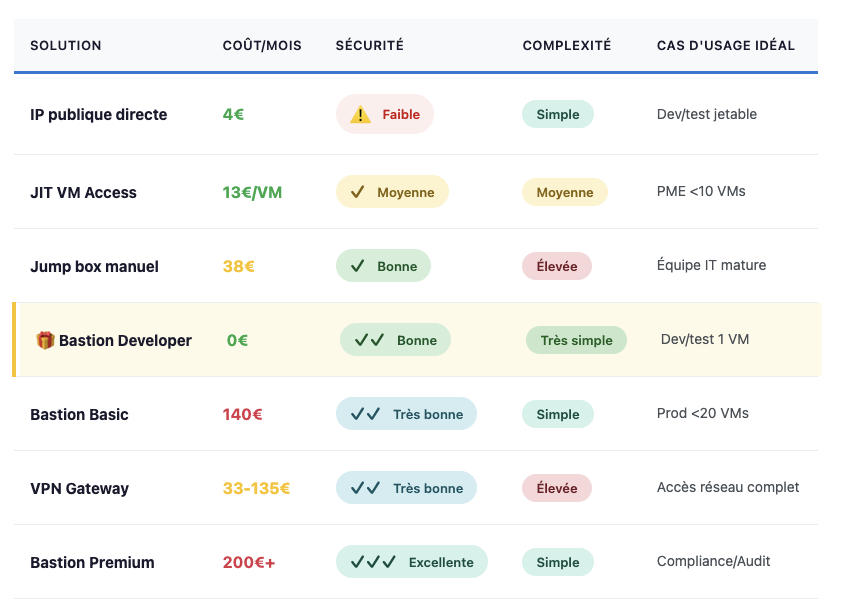
Use cases where Azure Bastion is the right choice
1. Strict regulatory compliance (health, finance, government)
Context: HIPAA, PCI-DSS, HDS, SecNumCloud sectors require proof of secure, auditable access to servers.
Why Bastion:
- Bastion Premium with Session Recording records all admin sessions on video
- Detailed logs in Azure Monitor (who connected, to which VM, when, duration)
- No public IP exposed = immediate compliance with "no direct Internet access" requirements
- Certificates supplied: ISO 27001, SOC 2, meet audit requirements without additional documentation
ROI: passing a compliance audit without Bastion = 5-10 man-days of preparation (manual logs, hardened jump boxes, documentation). Bastion = 0 days. The investment of €200/month pays for itself in 1 audit.
2. Companies without a dedicated infrastructure team
Context: tech startup, SME, autonomous dev teams. No resources to maintain a jump box.
Why Bastion:
- Zero-ops: Microsoft manages patching, HA, scaling, security
- Deployment in 5 minutes (vs. 2 hours for a well-configured jump box)
- No training required: same UX as standard Azure portal
ROI: engineer's time = 60€/hr. Maintaining a jump box = 3h/month (patching, monitoring) = 180€. Bastion Basic at €140/month = savings + superior security.
3. Multi-region environments with VNet peering
Context: distributed infrastructure, VMs in 5 Azure regions with hub-and-spoke peering.
Why Bastion Standard:
- IP-based connection: a single Bastion in the VNet hub accesses VMs from all peered spokes
- No need to deploy 5 regional Bastions (savings of 4 x €140 = €560/month)
- Centralized access management
Architecture: Bastion in VNet Hub (primary region) → connection to 200 VMs spread over 5 regions via peering. Savings: 1 Bastion at €140 vs. 5 Bastions at €700 = €560/month savings.
4. Massive remote working (COVID-like scenarios)
Context: 100 employees need to access Azure VMs from home, unpredictable dynamic IPs.
Why Bastion:
- No source IP whitelist to maintain (nightmare with dynamic residential IPs)
- Azure AD authentication: Automatic MFA, Conditional Access policies
- HTTPS/443 connection: passes all corporate and residential firewalls
VPN alternative: requires installing and configuring 100 VPN clients, managing certificates, user support. Bastion = 0 client installation.
Limits, frustrations and situations where Bastion is NOT the solution
1. Cost for small environments
Problem: €140/month to protect 2 dev VMs used 5h/week = €700/year for a non-existent problem.
Réalité : pour <5 VMs non-critiques, Bastion Developer gratuit ou JIT VM Access à 13€/VM/mois sont infiniment plus pertinents.
Common mistake: IT department imposes "everything must go through Bastion" without analyzing the need. Result: 3 dev environments with Bastion Basic = €420/month wasted.
2. Degraded performance for intensive graphics
Problem: RDP via Bastion aggressively compresses the video stream. CAD applications, 3D design, video editing = catastrophic experience.
User tests: CAD engineer reporting latency of 200-400ms and pixelation during 3D rotations in SolidWorks via Bastion. In direct public IP: 20ms latency, perfect fluidity.
Workaround: use Bastion for administration only, deploy a dedicated GPU VM with public IP + ultra-restrictive NSG for graphics work.
3. Multiple simultaneous connections from one workstation
Limitation: connection via Azure portal = 1 session per browser. To open 5 VMs in parallel, you need 5 private browser windows or 5 different browsers.
Partial solution Switch to native client with Bastion Standard, but requires Azure CLI and commands az network bastion rdp/ssh.
User frustration: administrators used to MultiTab RDP (multiple connections in a single client) have to change their workflows.
4. IPv6 not supported
Status: October 2025, Bastion only supports IPv4. Impossible to assign a public IPv6 IP or to connect to dual-stack VMs in IPv6.
Impact: organizations migrating to IPv6-only are blocked. Microsoft says "roadmap future", no date announced.
5. No Azure Virtual Desktop (AVD) support
Official limitation: Azure Bastion does not work with AVD (formerly Windows Virtual Desktop). Documented in the FAQ.
User confusion: "Why can I connect to a Windows VM via RDP but not to an AVD which is... also Windows RDP?" Difference in architecture: AVD uses its own gateway.
6. Limited file transfer
Via portal: impossible to transfer files (no drag-and-drop, no shared drives).
Via native client: transfer possible, but max 100 MB per file with Standard SKU. For 4 GB ISOs or 20 GB SQL dumps, use Azure Files/Blob Storage.
Frustration: admin who just wants to "copy a 50 Kb config file" has to use a native client + complex CLI command instead of a simple Ctrl+C / Ctrl+V.
Deployment: a pragmatic guide to avoid screw-ups
Technical requirements
Correctly dimensioned VNet:
- Subnet /26 minimum for AzureBastionSubnet = 64 IPs
- Recommended /25 or /24 if scaling is planned (50 instances max)
- The subnet may contain NO other resources (NSG Ok, UDR forbidden, VMs forbidden).
Subnet name : must called exactly AzureBastionSubnet (significant breakage). azurebastionsubnet or Azure-Bastion-Subnet = deployment error.
Standard public IP SKUs: Basic/Standard/Premium require a Standard public IP (not Basic). Static allocation. Developer does not.
RBAC Permissions : Microsoft.Network/virtualNetworks/write, Microsoft.Network/virtualNetworks/subnets/join/action, Microsoft.Network/publicIPAddresses/*. Without these perms, deployment fails silently.
SKU selection strategy
Use Developer if:
- Dev/test environment
- Connexions occasionnelles (<10h/semaine)
- Tight budget
- Only one person can log on at a time
Use Basic if:
- SME production
- <20 VMs
- Portal connections are all you need
- No need for video audit
Use Standard if:
20 VMs or multi-region peered
- Native client connection required
- Regular file transfer
- Scaling planned (>20 concurrent connections)
Use Premium if:
- Compliance requiring session recording
- Regulated sectors (finance, healthcare, defense)
- Private-only architecture (zero public IP)
Deployment checklist
- Create subnet VNet > Subnets > Add > Name =
AzureBastionSubnetSize /26 - Public IP provisioning: Standard SKU, Static, same region as VNet
- Deploy Bastion: Azure Portal > Create Resource > Bastion > Select SKU
- Wait 5-10 minutes: managed instances are deployed
- Test connection: VM > Connect > Bastion > Enter credentials
- Configuring NSG on AzureBastionSubnet (optional but recommended) :
- Inbound: Allow HTTPS (443) from GatewayManager tag
- Outbound : Allow RDP (3389) and SSH (22) to VirtualNetwork tag
- Activate Diagnostic Logs: Bastion > Diagnostic settings > Send to Log Analytics
Post-deployment monitoring and optimization
Key metrics to monitor:
- Active sessions: growing trend = need for scaling
- Connection error rate: >5% = NSG or VM config problem
- Bandwidth usage: anticipate data transfer costs
Alerts to be configured:
- Instances >80% (near saturation)
- Repeated authentication failures (intrusion attempts)
- Bastion configuration change (audit unauthorized modifications)
Cost optimization:
- Remove Bastion from unused environments (weekend dev)
- Use Azure Automation to deploy/remove Bastion according to a schedule (working hours only)
- Consolidate several small regional Bastions into a single peering hub
Is Bastion worth it in 2025?
Azure Bastion is neither a universal miracle nor a Microsoft rip-off. It's a specialized security tool that excels in specific contexts and becomes a budgetary liability when misused.
Bastion is worth the investment if:
- You have strict compliance requirements (audit, session registration)
- Your team doesn't have the skills or time to maintain a jump box
- You manage 20+ VMs in production with multiple administrators
- You need to support nomadic users with dynamic IPs
- Your CIO categorically refuses to accept exposed public IPs (and he's right).
Bastion is a waste if:
- You have 2-3 sporadically used dev VMs → use free Developer
- You already have a functional, high-performance VPN → no need for Bastion
- Vous gérez <10 VMs sans contraintes réglementaires → JIT VM Access suffit
- You have a skilled OPS team and time → jump box manual costs 4x less
- You do graphics-intensive work (CAD, 3D) → unacceptable latency
Fatal mistakes to avoid:
- Deploy Bastion Basic to test → forget → pay €1680/year for nothing
- Impose Bastion everywhere "on principle" without cost/benefit analysis
- Choose Premium without Session Recording (no extra charge of €60/month)
- Deploy 1 Bastion per region, whereas peering only requires one
Optimum strategy 2025:
- Dev/Test: Bastion Developer free
- Production <20 VMs : Bastion Basic ou JIT VM Access (selon compliance)
- Production >20 VMs: Bastion Standard with IP-based connection
- Regulated sectors: Bastion Premium with Session Recording
- Special cases: combine JIT + Bastion (JIT opens temporary access, Bastion routes secure connection)
The true ROI of Bastion is not measured in euros saved on licenses, but in risks avoided (intrusion, compromise), time saved (no jump box maintenance), and compliance facilitated (auditing without suffering).
If a single security incident costs you €50k in investigation + remediation + loss of customer confidence, Bastion Basic's €1680/year is cheap insurance. But if you're securing disposable dev VMs with no sensitive data, it's like insuring a Twingo at Ferrari prices.
Next steps:
- List all your exposed VMs with public IP + open RDP/SSH
- Categorize: critical (prod, sensitive data) vs. non-critical (dev, test)
- Deploy Bastion Developer free of charge on non-criticals for testing purposes
- Calculate the cost of a security incident (ransom, downtime, legal)
- Decide: Bastion Basic (140€/month) or incident risk (potentially 50k€+)
Azure Bastion is an adult solution for adult problems. If your Azure infrastructure is a hobby, you don't need it. If it's your business, €140/month for peace of mind is a no-brainer.
.svg)






.svg)