Microsoft Sentinel is Microsoft's cloud-native SIEM (Security Information and Event Management), merged with SOAR (Security Orchestration, Automation and Response) and UEBA (User and Entity Behavior Analytics) capabilities. Launched in 2019 as Azure Sentinel, repositioned in 2024 within the Microsoft Defender portal, Sentinel collects, analyzes and correlates cloud-scale security logs to detect threats, intrusions and anomalous behavior.
The sales pitch: "unlimited SIEM, cloud elasticity, integrated AI, simple per-GB pricing". The reality on the ground: unpredictable monthly bill that doubles in 3 months if ingestion is not mastered, steep KQL (Kusto Query Language) learning curve, and a pricing trap where verbose network logs can cost €15,000/month while their detection value is virtually nil.
Between Splunk at €500k/year (rigid licensing, cumbersome installation) and Sentinel marketed as "flexible and economical," the choice seems obvious. But what Microsoft doesn't mention is that Sentinel becomes more expensive than Splunk beyond 500 GB/day of poorly optimized ingestion. This article reveals the true cost of Sentinel, compares it objectively with Splunk/QRadar, explains how to avoid the $50k/month bill, and, most importantly, calculates whether your organization really needs a SIEM or if an EDR + centralized logs are sufficient (spoiler: 60% of SMEs do not need SIEM).
What is Microsoft Sentinel and how does it really work?
Architecture and positioning
Sentinel is not software to be installed, but an Azure SaaS service based on three components:
Azure Monitor Log Analytics Workspace: storage backend. All logs ingested into Sentinel transit and are indexed in Log Analytics. Herein lies the pricing confusion: you pay for Log Analytics + Sentinel as combined third parties (simplified since 2023), but there are additional costs (retention, archiving, restoration).
Correlation and analytics engine: detection rules written in KQL (Kusto Query Language, Microsoft's SQL). Sentinel includes 300+ pre-configured rules (MITRE ATT&CK attacks, abnormal behavior, indicators of compromise) + possibility of creating custom rules. Integrated machine learning to detect anomalies (connections from unusual geolocation, peak user activity at 3 a.m.).
SOAR and automation: playbooks based on Azure Logic Apps. When an alert is triggered (e.g.: bruteforce RDP attempt), a playbook can automatically block the IP in the firewall, create a ServiceNow ticket, send Teams notification to the SOC. Savings: 70% of level 1 responses automated.
Integration Defender XDR: since 2024, Sentinel runs in the Microsoft Defender portal. Merger with Defender for Endpoint, Defender for Cloud, Defender for Identity. Unified vision: endpoint, identity, cloud, on-premise in a single pane of glass.
Data tiers: Analytics vs Data Lake (new in 2025)
Analytics tier: high-value logs (authentication, EDR alerts, threat intelligence). Real-time analysis, correlation, detection. Free 90-day retention. Cost: €2.76/GB (Pay-As-You-Go Western Europe) or €342/day for 100 GB in commitment tier.
Data Lake tier (preview October 2025): long-term storage of high-volume, low-value logs (firewall verbose, web proxy, network flow). Cost: 0.19€/Gb (85% cheaper than Analytics). Free 30-day preview retention. Usage: forensics, compliance, occasional queries. No real-time detection.
Optimal logic: ingest Windows Security Events, Azure AD logs, EDR alerts into Analytics tier. Switch Palo Alto verbose firewall logs (50 GB/day) to Data Lake. Savings: 50 GB x €2.76 = €138/day in Analytics vs. 50 GB x €0.19 = €9.50/day in Data Lake = €129/day saved (€3870/month).
Connectors and data sources
Native Microsoft connectors (free to ingest):
- Azure Activity Logs (Azure resources audit)
- Microsoft 365 Audit Logs (Exchange, SharePoint, Teams)
- Microsoft Defender for Endpoint
- Azure AD Identity Protection
- Office 365 Advanced Threat Protection
With M365 E5/A5/G5 license: data grant of 5 MB/user/day. Organization 1000 users = 5 GB/day free for Microsoft 365 logs.
With Defender for Servers P2: 500 MB/VM/day free for server logs.
Third-party connectors (chargeable):
- Firewalls (Palo Alto, Fortinet, Checkpoint) via Syslog/CEF
- Proxies (Zscaler, Cisco Umbrella)
- Third-party EDR (CrowdStrike, SentinelOne) via API
- Cloud providers (AWS CloudTrail, GCP Audit)
- Legacy SIEM (Splunk, QRadar) for gradual migration
Connector traps: some send ultra-verbose logs. An unfiltered Palo Alto firewall = 200 GB/day of useless authorized traffic. Filter at collector level (deny logs only) = go from 200 GB to 5 GB/day.
KQL: the language that makes or breaks your experience
Kusto Query Language = SQL-like for querying logs. Syntax :
kusto
SecurityEvent
| where TimeGenerated > ago(24h)
| where EventID == 4625 // Failed logon
| summarize FailedAttempts = count() by Account, Computer
| where FailedAttempts > 10
| order by FailedAttempts desc
Learning curve: 2-3 weeks for a Windows admin. 1-2 months to master complex aggregations (join, union, parse). Mandatory for creating custom rules, tuning false positives, investigating incidents.
SPL (Splunk) comparison: KQL simpler for basic queries, less powerful for advanced transformations. Splunk SPL = more native functions, better community documentation.
Actual pricing and costing: the €50k/month trap
2025 pricing structure
Pay-As-You-Go:
- Analytics tier: €2.76/GB (Western Europe), €2.46/GB (US East)
- Data Lake tier: €0.19/GB (preview, free until March 2026)
- Retention >90 days: 0.10€/Go/month (Analytics), 0.02€/Go/month (Archive)
Commitment Tiers (capacity reservation) :
- 100 GB/day: €342/day = €10,260/month (-18% vs PAYG)
- 200 GB/day: €639/day = €19,170/month (-21%)
- 500 GB/day: €1437/day = €43,110/month (-27%)
- 1000 GB/day: €2666/day = €79,980/month (-32%)
Promo 50 GB/day (Oct 2025 - March 2026): discounted rate locked in until March 2027 for SME early adopters.
Hidden additional costs:
- Azure Logic Apps (SOAR playbooks): €0.00025/share. 10,000 executions/month = €2.50 (negligible).
- Archive search : 0,005€/Go scanned. Forensics on 5 TB archive = €25.
- Data Restore (Archive → Analytics): 0.10€/Gb. Bringing back 100 GB in hot tier = €10.
- Outgoing bandwidth: if you export logs to a third-party tool, egress Azure will be billed (first 100 GB free, then ~€0.08/GB).
Realistic monthly cost calculation
SME scenario 200 employees, hybrid cloud:
- Windows Event Logs (50 servers): 2 GB/day
- Azure AD Sign-ins: 1 GB/day (included free of charge E5)
- Microsoft 365 Audit: 1.5 GB/day (included free of charge in E5)
- Defender for Endpoint: 3 GB/day (included free with Defender for Servers)
- Fortinet firewall: 15 GB/day (filtered, deny only)
- Zscaler proxy: 5 GB/day
- Total Analytics tier: 27.5 GB/day
- Commitment tier 100 GB/day: €10,260/month (72.5 GB/day wasted)
- Pay-As-You-Go: 27.5 GB x €2.76 x 30 days = €2,277/month
Optimum option: PAYG + Data Lake for verbose firewall (if activated) = €2277/month.
Company scenario 2000 employees, multicloud:
- Server logs (300 VMs): 30 GB/day
- Azure + AWS + GCP audit logs: 20 GB/day
- Multi-platform EDR: 40 GB/day
- Network logs (firewalls, IDS/IPS): 200 GB/day → switch to Data Lake
- Proxy and DNS: 50 GB/day → Data Lake
- Analytics tier: 90 GB/day x €2.76 x 30 = €7452/month
- Data Lake tier: 250 GB/day x €0.19 x 30 = €1425/month (special offer)
- Total: 8877€/month vs 340 Go PAYG Analytics = 28 152€/month. Savings: €19,275/month.
Nightmare scenario: non-optimized ingestion:
- Firewall logs ALL traffic (authorized + deny): 500 GB/day
- Unfiltered debug application logs: 200 GB/day
- Duplicate logs (sent from 2 sources): 100 GB/day
- Total: 800 GB/day x €2.76 x 30 = €66,240/month
Lesson: filter at source, activate Data Lake, monitor daily ingestion. Sentinel without governance = money pit.
Free trials and data grants
Trial 31 days: 10 GB/day free per workspace (max 20 workspaces/tenant). Cost Log Analytics + Sentinel waived. Perfect for POC.
Data grants M365 E5: 5 MB/user/day. 2000 users = 10 GB/day free M365 logs. Over 1 year: savings 10 GB x €2.76 x 365 = €10,074.
Data grants Defender for Servers P2: 500 MB/VM/day. 300 VMs = 150 GB/day free. Annual savings: 150 GB x €2.76 x 365 = €151,110.
Strategy: maximize data grants, reserve commitment tier on paid logs only.
Sentinel vs Splunk vs QRadar: battle of the SIEM giants
Splunk Enterprise Security: the flexible behemoth
Strengths:
- SPL (Search Processing Language): the most powerful of SIEM query languages
- 2800+ Splunkbase apps (community integrations)
- On-premise, cloud, hybrid: deployment everywhere
- Risk-Based Alerting (RBA): reduces alerting volume by 90% via cumulative risk scoring
- Native MITRE ATT&CK aligned detection
Weaknesses:
- Prohibitive cost: €150/GB (classic licensing) or complex workload pricing
- Heavy infrastructure: indexers, search heads, forwarders to manage (except Splunk Cloud)
- Steep SPL learning curve (but massive community)
Pricing Splunk:
- Ingestion 200 GB/day = ~30k€/month (licensing) + infra (10-15k€/month) = 40-45k€/month
- Same Sentinel PAYG volume: 200 GB x €2.76 x 30 = €16,560/month
When to choose Splunk: if heterogeneous stack (multi-vendor, legacy on-prem), advanced SPL needs, budget >500k€/year, Splunk expert SOC team.
IBM QRadar SIEM: the structured veteran
Strengths:
- Licensing EPS (Events Per Second): predictable (but rigid)
- Correlation engine mature (offense ranking)
- Strong compliance (finance, government)
- Support for physical appliances (sovereign datacenters)
Weaknesses:
- Monolithic architecture (difficult scaling)
- Aging UX (slow improvements)
- Limited integrations (600 vs. 2800 Splunk)
- Weak cloud-native (late catch-up)
Pricing QRadar:
- Licensing ~€15k/year for 5000 EPS
- 200 GB/day ≈ 20 000 EPS = 60k€/year licensing + appliance (20k€) = 80k€/year or 6666€/month
When to choose QRadar: regulated environments (banking, OIV), sovereign on-premise requirements, EPS licensing preferred for large volumes.
SIEM 2025 comparison
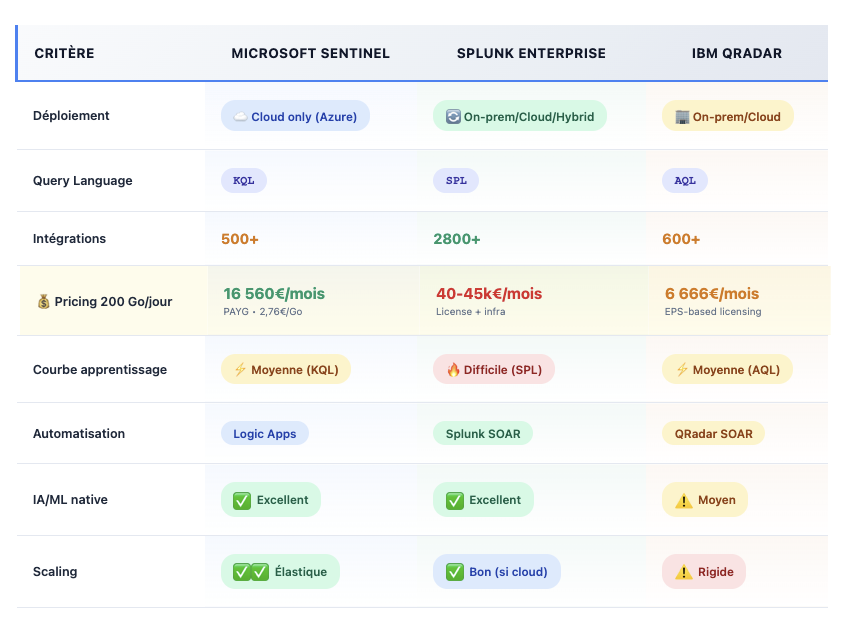
Objective verdict:
- Sentinel: unbeatable for Microsoft-first organizations (Azure, M365), controlled budgets with data grants, need for cloud elasticity
- Splunk: functional leader, complex heterogeneous environments, budgets >500k€/year, SPL expertise available
- QRadar: ultra-regulated sectors, preferred EPS licensing, sovereign on-premise infrastructure
Real use cases and ROI calculation
Use case 1: Identity compromise detection (Azure AD)
Context: attacker steals employee credentials via phishing. Connection from IP Russia at 2am.
Sentinel detection:
- Analytics rule: Azure AD connection from unusual country + abnormal time
- UEBA: user scoring increased from 0 to 85/100 (high risk)
- Alerte générée en <2 minutes
- Playbook auto: revoke session, force MFA re-auth, notify manager + SOC
Without SIEM: manual detection via daily Azure AD log review (if done) = 24-48h delay. Attacker exfiltrates emails, accesses sensitive SharePoint.
ROI: incident avoided = 150k€ (forensics, IP loss, RGPD notification). Sentinel cost: 2000€/month. Payback: 1 major incident avoided/year.
Use case 2: Detecting ransomware propagation
Context: ransomware infects user workstation, starts network encryption via SMB.
Sentinel detection:
- Defender for Endpoint alert: suspicious behavior (mass file encryption)
- Sentinel correlation: same user accesses 50+ servers in 10 minutes (abnormal)
- Network logs: peak SMB outbound traffic from infected workstation
- Merger alert: ransomware propagation underway
- Playbook: isolates workstation, blocks AD user, snapshots critical VMs
Detection delay: 8 minutes. Containment: 15 minutes. Infected servers: 3. Impact: 50k€ (recovery of 3 servers).
Without SIEM: detection on D+2 (users report encrypted files). 200 servers impacted. Cost: €2M (downtime, recovery, potential ransom).
ROI: major incident avoided (savings €1.95M) vs Sentinel annual cost €24k. ROI: 8000%.
Use case 3: Compliance and audit (RGPD, ISO 27001)
Context: ISO 27001 audit requires proof of monitoring access to personal data.
Sentinel:
- Tracking of all customer SQL database access (query audit logs)
- Alerting out-of-hours access (22h-6h)
- Monthly reporting: who accessed what, when
- Retention 13 months (compliance)
ISO audit: auditor asks "show me customer database access over 12 months". Sentinel: report generated in 5 minutes (KQL query).
Without SIEM: scattered logs (SQL Server, application, AD). Manual aggregation = 40h/year. Cost: €4000 (engineer time). Risk of non-compliance if logs incomplete.
ROI: saving on audit time (€4000/year) + coverage of non-compliance risk (potential fines).
Zero value use case: unnecessary over-ingestion
Anti-pattern: ingest ALL logs from ALL systems "just in case".
Real-life example: company ingests :
- Verbose IIS logs (every HTTP 200 OK): 300 GB/day
- Application debug logs: 150 GB/day
- DNS query logs (all queries): 200 GB/day
- Total: 650 GB/day x €2.76 x 30 = €53,820/month
Detection value: 5% of ingested logs trigger alerts. 95% = useless noise.
Optimization:
- IIS: logger errors 4xx/5xx only = 300 GB → 5 GB
- App debug: disable in prod, enable on-demand = 150 GB → 0 GB
- DNS: logger denied queries only = 200 GB → 3 GB
- After optimization: 8 GB/day x €2.76 x 30 = €662/month
Savings: €53,158/month (97% reduction) without loss of detection capability.
Deployment and pitfalls to avoid
Mistake 1: Deploying without an ingestion strategy
Problem: activate all connectors "to see". Bill multiplied by 10 months 2.
Best practice:
- Identify 5-10 critical log sources (AD, EDR, critical firewalls)
- Calculate expected volume (7-day pilot monitoring)
- Define maximum monthly budget (e.g. €5,000)
- Activate progressively, measure ROI detection by source
Error 2: Neglecting M365/Defender data grants
Problem: paying to ingest Microsoft logs when they're free with existing licenses.
Check: your M365 E5 or Defender for Servers P2 licenses? Activate data grants. Potential savings: €50-150k/year.
Error 3: Analytics rules not tuned
Problem: default Microsoft rules generate 500 alerts/day, 90% false positives. SOC overwhelmed, real threats drowned out.
Mandatory tuning:
- 1st month: audit mode, no alerting
- Analyze false positive patterns
- Adjust thresholds (e.g. 10 failed logins → 50 failed logins if legacy apps are noisy)
- Whitelist IP/known users
- Result : 500 alerts/day → 20 alerts/day, 80% true positives
Error 4: Forgetting retention and archiving
Problem: compliance requires 12 months logs. Free analytics retention for 90 days, after that = 0.10€/Go/month.
Calculation: 100 GB/day x 9 additional months x 30 days = 27,000 GB x €0.10 = €2,700/month retention.
Solution: after 90 days, switch to Archive tier (€0.02/GB/month). Same volume = €540/month. Savings: €2160/month.
Error 5: Underestimating KQL skills
Problem: SOC does not master KQL. Incidents not effectively investigated, MTTR (Mean Time To Respond) x3.
Training required:
- 3 days KQL basics (free Microsoft Learn)
- 2 weeks investigative practice (labs)
- SC-200 certification (Microsoft Security Operations Analyst)
Alternative : externaliser SOC (Managed Sentinel). Coût : 5-15k€/mois selon SLA. Pertinent si <3 FTE SOC internes.
Sentinel: investment or trap?
Microsoft Sentinel is neither marketing's miracle cloud-economy SIEM, nor a pricing scam. It's a powerful tool for Microsoft-centric organizations with ingestion discipline.
Sentinel makes sense if:
- Dominant Microsoft stack (Azure, M365, Defender)
- Active data grants (E5, Defender for Servers) = immediate ROI
- Volumétrie <300 Go/jour optimisée (Analytics + Data Lake)
- Available KQL skills or Managed SIEM budget
- Need for elasticity (temporary intake peak, rapid scale)
Sentinel is a trap if:
- Uncontrolled ingestion (any logger without filter)
- Multi-vendor heterogeneous stack (Splunk better)
- Volume >500 GB/day poorly optimized (explosive cost)
- No KQL skills (blocking learning curve)
- 100% on-premise sovereign environment (QRadar/Splunk better)
Realistic ROI:
- Investment: €2,000-10,000/month depending on volume
- Gains: 1-2 major incidents avoided/year (150k€-2M€), compliance facilitated (4-10k€/year), L1 automation (30% SOC time savings)
- Payback: 3-6 months if intake optimized, never if volume drifts
The real question: do you need a SIEM?
You do NOT need SIEM if:
- PME <100 employés, infrastructure simple (cloud SaaS uniquement)
- Modern EDR is sufficient (Defender for Endpoint, CrowdStrike)
- Basic centralized logs OK (Azure Monitor, CloudWatch)
- No strong compliance obligations
You NEED SIEM if:
200 employees, hybrid/complex infrastructure
- Regulated compliance (ISO 27001, NIS2, PCI-DSS)
- Dedicated SOC team or outsourcing
- Critical multi-source correlation (not just EDR)
60% cheaper alternative: if you don't need a full SIEM, Microsoft Defender XDR (without Sentinel) + centralized Azure Monitor logs = €500-1500/month vs €5000-10,000/month Sentinel.
Next pragmatic steps:
- Audit current stack: which critical logs? Expected volume?
- Activate trial Sentinel 31 days: POC on 3-5 priority sources
- Calculate real cost: PAYG vs Commitment vs Data Lake, include data grants
- Testing detection rules: false positives? True alerts? Tuning necessary?
- Form KQL team: 2 people minimum (skill redundancy)
- Decide: Sentinel full, Defender XDR only, or Splunk/QRadar if better fit
Fatal mistake: deploying Sentinel without ingestion governance + without KQL skills = €50k/month bill with no detection value. Success: targeted strategy, optimized ingestion, continuous tuning = ROI 500-1000% over 3 years.
Microsoft Sentinel is an excellent cloud SIEM for those who know how to use it. For the rest of us, it's a money-spinner that detects as many threats as a basic firewall at 1/10th the price. Choose wisely.
.svg)






.svg)